AMD Zen x86 Core Exclusive SME & SEV Encryption Features Detailed

With the increase in system complexity and growth of the cloud, the need for security in the enterprise segment is greater than ever. Since a major chunk of AMD’s revenue comes from this segment, the company is bound to take these challenges seriously, and so it has developed new memory encryption technologies that will debut with the forthcoming AMD Zen x86 CPU core architecture.
The technologies are categorized into two broad features: SME (Secure Memory Encryption), and SEV (Secure Encrypted Virtualization). Before I go into detail on these features, I want to mention that both SME and SEV are exclusive to AMD Zen right now, and no competing Intel architecture – be it Skylake or Kaby Lake – has something like this on board.
AMD Secure Processor Built Right into The Hardware
The advanced encryption features are offered via a dedicated “AMD Secure Processor” integrated within the Zen chip. This Secure Co-Processor is based on ARM TrustZone, a system-wide approach to security, that runs on top of the hardware and partitions the CPU into two virtual “worlds.” AMD explains these “worlds” as follows:
Sensitive tasks are run on the AMD Secure Processor – in the “secure world” – while other tasks are run in “standard operation.” This helps ensure the secure storage and processing of sensitive data and trusted applications. It also helps protect the integrity and confidentiality of key resources, such as the user interface and service provider assets.
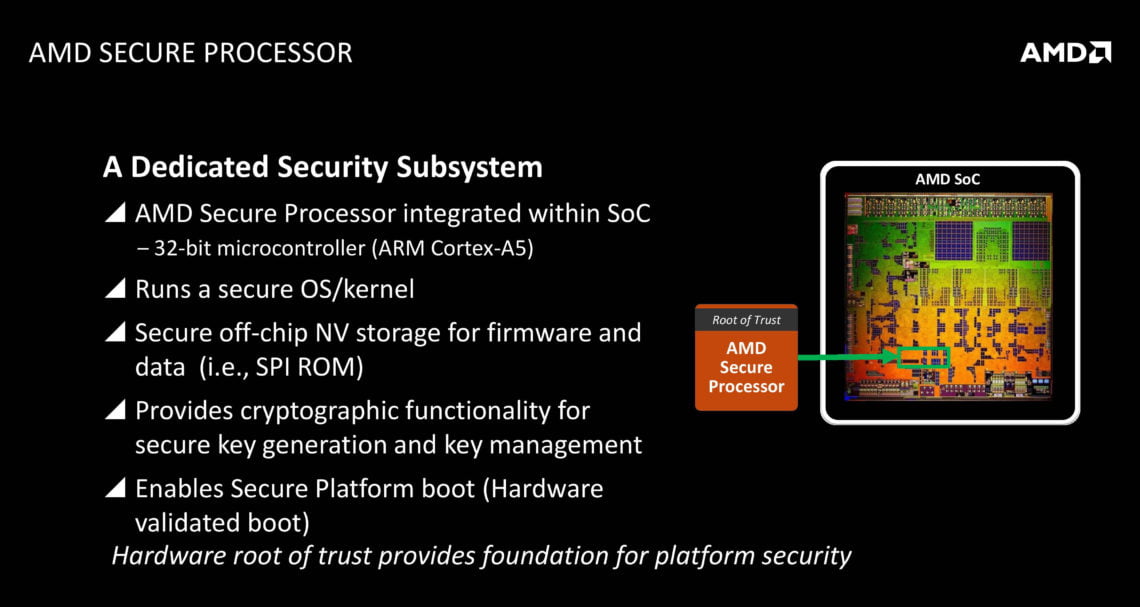
Moreover, the AMD Secure Processor doesn’t need any application software modifications, and is designed to be flexible to address security needs across a variety of systems – from embedded to high-end server workloads.
AMD Zen SME & SEV – Major Steps Forward in End-to-End Computer Security
We know that the data is typically encrypted when stored on disk; however the DRAM has it in clear text format. This can leave the data vulnerable to unauthorized use, and making the things even worse is the new non-volatile memory technology (NVDIMM). Unlike inherently volatile DIMMs, non-volatile memory doesn’t lose all data which means once an attacker has physically removed an NVDIMM chip, they would be able to access everything inside – including sensitive data, passwords, or secret keys – in an unencrypted format.
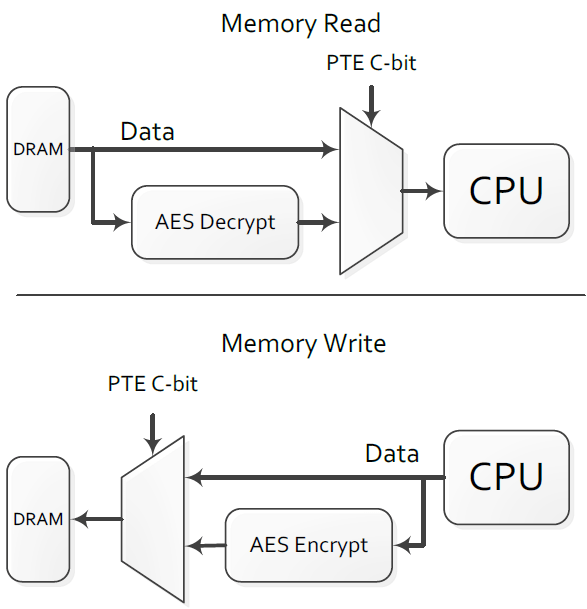
What the AMD Zen Secure Memory Encryption (SME) does is that it allows for the complete encryption of the main memory. You will be able to ensure a true end to end security by closing the last remaining “cleartext” portion as well as enabling encryption in the memory.
Main memory encryption is performed via dedicated hardware in the on-die memory controllers. Each controller includes a high performance Advanced Encryption Standard (AES) engine that encrypts data when it is written to DRAM, and decrypts it when read as shown. The encryption of data is done with a 128-bit key.
Moving to the Zen Secure Encrypted Virtualization (SEV), this is designed to integrate main memory encryption capabilities with the existing AMD-V virtualization to support running multiple VMs under the control of a hypervisor. The technique enhances isolation of VMs, hence protecting against administrator tampering, and untrusted hypervisor.
When enabled, SEV hardware tags all code and data with its VM ASID which indicates which VM the data originated from or is intended for. This tag is kept with the data at all times when inside the SOC, and prevents that data from being used by anyone other than the owner. While the tag protects VM data inside the SOC, AES with 128 bit encryption protects data outside the SOC.
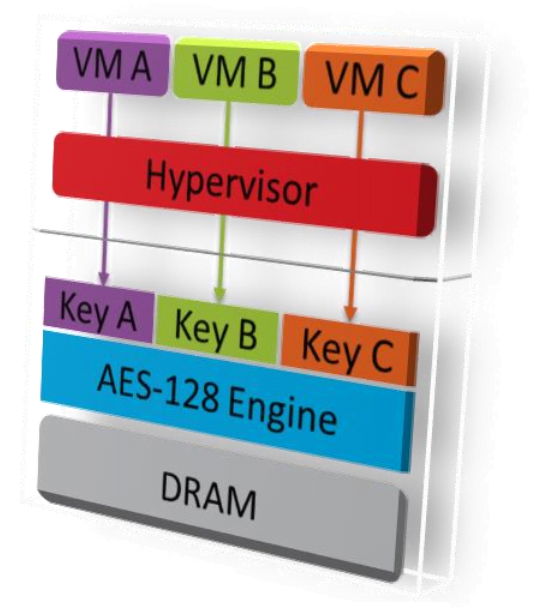
The SEV does indeed represent “a new virtualization security paradigm” in the world of cloud computing where it allows end users to encrypt the entire instance of virtualization. Even the hypervisor and administrator of the cloud system will not be able to inject a malicious code into a guest VM, if they intended to do so.